Use Case: You have created AWS kubernetes cluster (private topology) using kops. The nodes created will be in private subnet. Bastion box in public subnet is required to access the nodes. While creating the cluster, kops is fed with your own ssh public key (~/.ssh/id_rsa.pub) using –ssh-key-name parameter. Once cluster is ready you can access Bastion box from your local laptop and then from the bastion box you can login to the cluster node.
Problem: To access the node you have to provide the private key when initiating connection on the bastion box using ssh. Keeping a copy of private key on the bastion is not secure. Anybody who has access to the bastion box can access the cluster node.
Solution: You can still login to node on the bastion box without keeping copy of the private key on the bastion. This is possible by using agent forwarding feature. In this article I will show this using PuTTYgen, PuTTY and Pageant app utility.
Steps:
In this example
PuTTY is on my laptop
Bastion box is bastion.amazonaws.com
Cluster Node IP is 172.16.152.235
>>Install PuTTYgen and PuTTY on your laptop
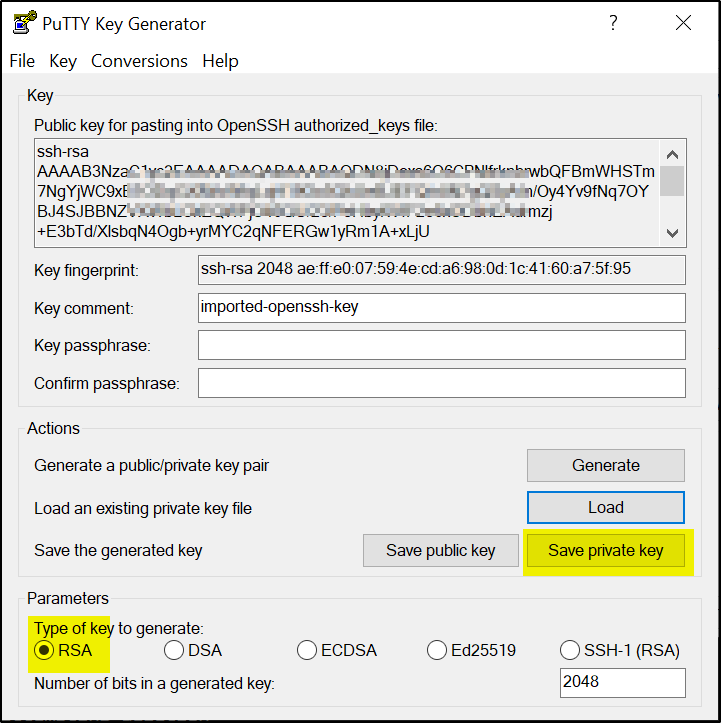
>>Open PuTTYgen and load the ssh private key, default name is id_rsa (if you have not changed the name while generating it)
>>Save the private key as .ppk file. This .ppk key will be used in PuTTY.
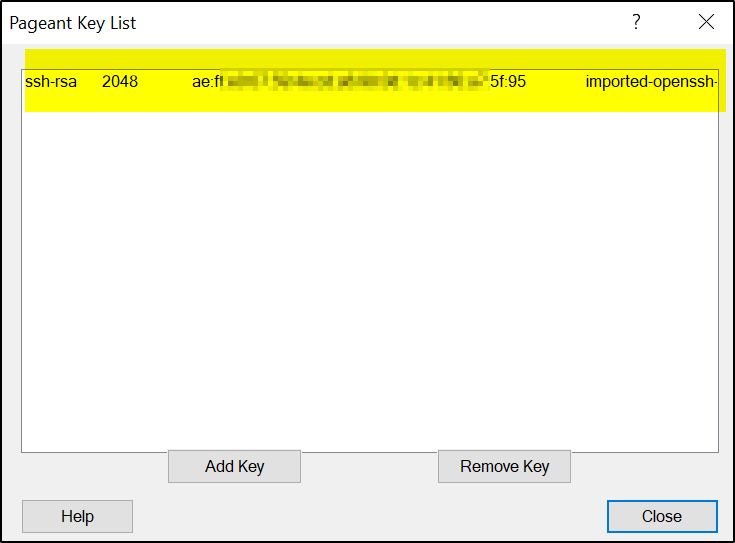
>> Now open Pageant exe (you can find it in C:\Program Files\PuTTY path)
When you run Pageant, it will put an icon of a computer wearing a hat into the System tray. It will then sit and do nothing, until you load a private key into it. If you click the Pageant icon with the right mouse button, you will see a menu. Select ‘View Keys’ from this menu. The Pageant main window will appear. The Pageant window contains a list box. This shows the private keys Pageant is holding. When you start Pageant, it has no keys, so the list box will be empty. To add a key to Pageant, press the ‘Add Key’ button. Pageant will bring up a file dialog, labelled ‘Select Private Key File’. Find your private key file in this dialog, and press ‘Open’. Pageant will now load the private key. If the key is protected by a passphrase, Pageant will ask you to type the passphrase. When the key has been loaded, it will appear in the list in the Pageant window.
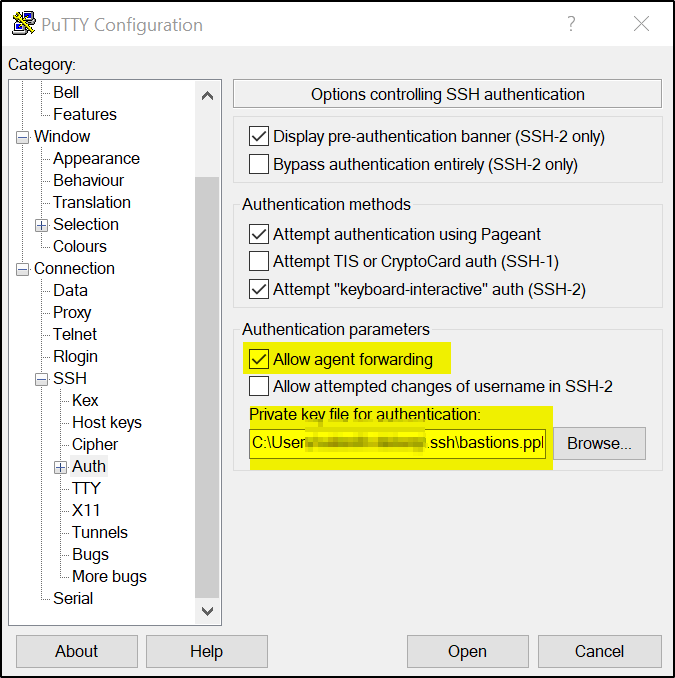
>>Configure PuTTY as shown
>>Save the default setting, then go to SSH–>Auth–>browse and select the .ppk file created earlier and check the “Allow agent forwarding” checkbox
>>Now click on Session and Save the settings again and click Open
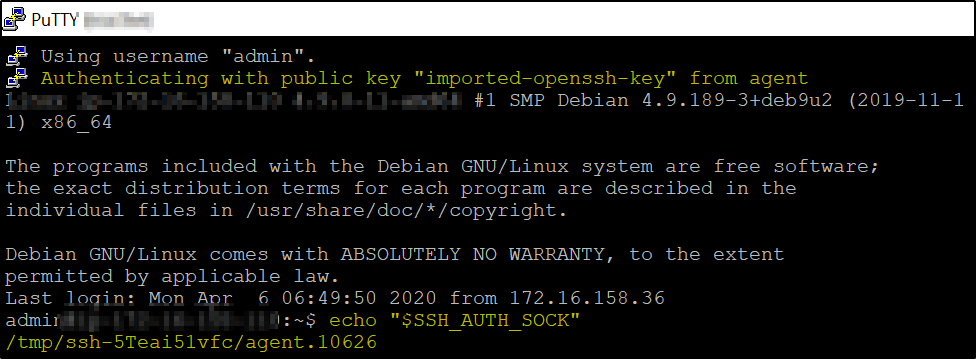
>>It will connect to Bastion box
Check that it shows – “Authenticating with public key “imported-openssh-key” from agent
Run – echo “$SSH_AUTH_SOCK”
If the result line comes up blank, agent forwarding has not been enabled at all.
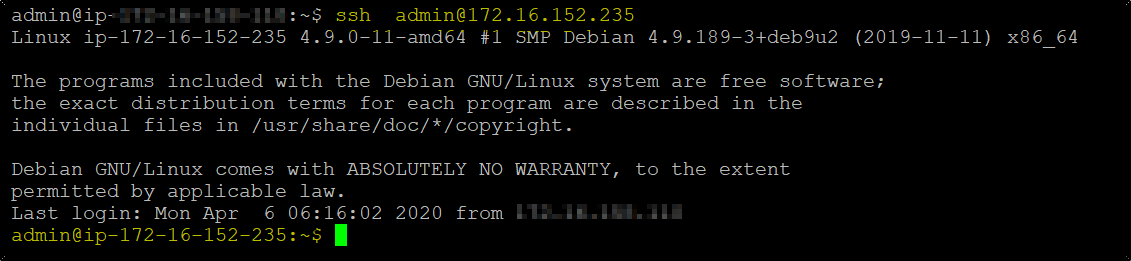
>> Now if you run ssh on the Bastion server and use it to connect to cluster Node in private subnet-
This way the private key is not copied to Bastion box and still private cluster node is accessed.