In part 1, you configured Azure Service Principal for use with API Gateway, in part 2, you configured an API using API Gateway, and in part 3, you created the custom authorizer that can be used to retrieve the appropriate policies when your API receives an access request. Now we will see how to use the custom authorizer to secure your API’s endpoints.
Log in to AWS and navigate to the API Gateway Console.
Based on which method you want to secure using custom authorizer, you can set it on that method. Multiple methods can be secured by same custom authorizer but you have to set it on each of those methods.
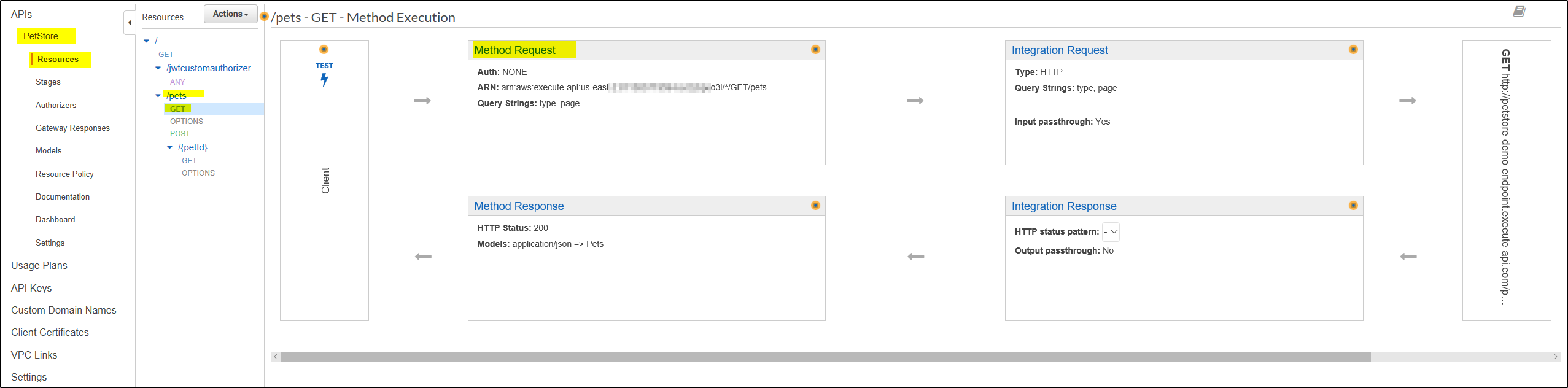
Go to PetStore API–> Resources –> /pets –> Get –> Click on Method Request
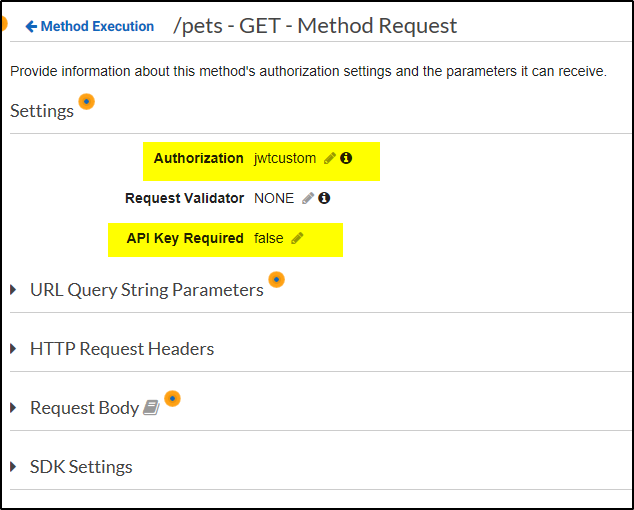
Under Settings, Click pencil icon to the right of Authorization and choose the custom authorizer you created. Click the check tick mark icon to save and make sure API Key Required field is set to False (if your custom authorizer is not visible then just refresh the API gateway link again)
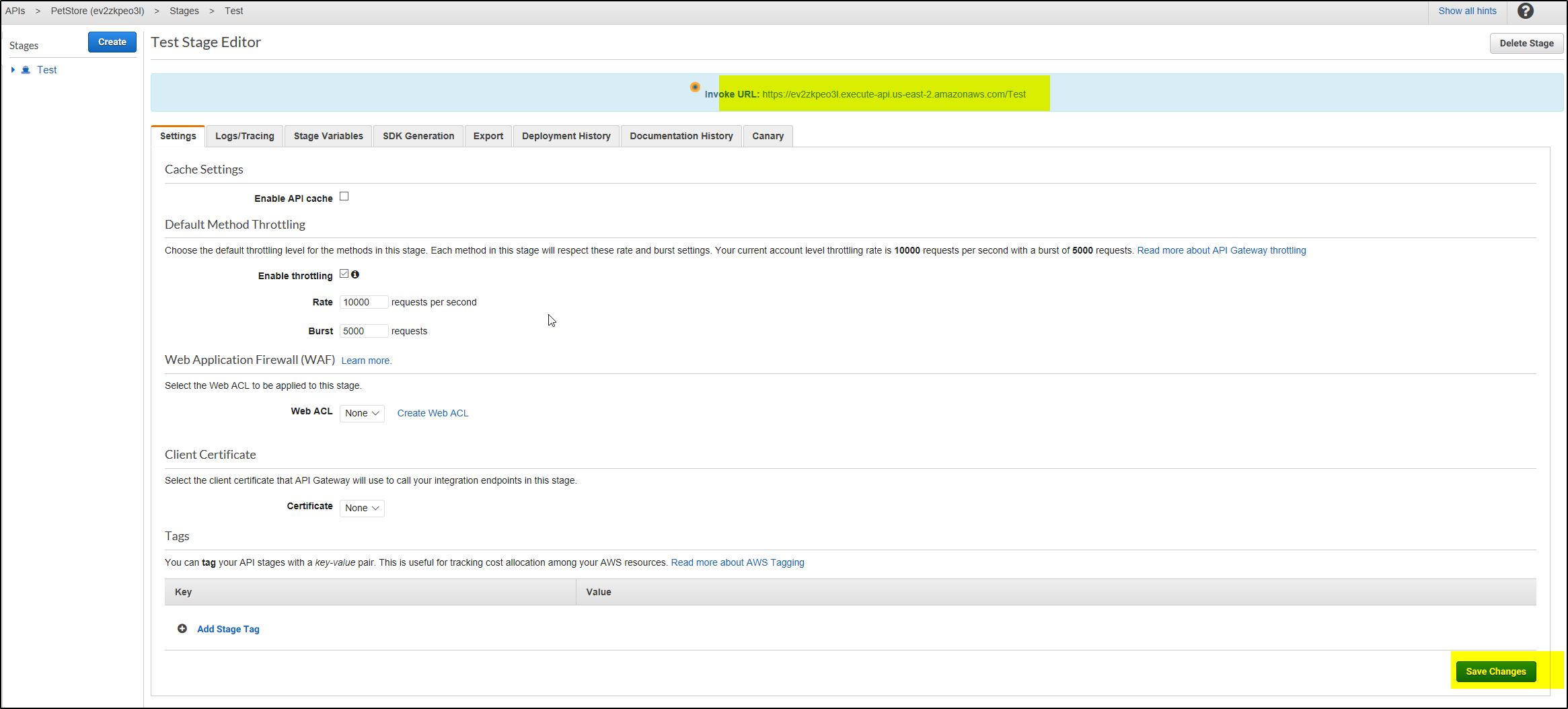
Deploy the API
To make your changes public, you’ll need to deploy your API.
If successful, you’ll be redirected to the Test Stage Editor. Copy down the Invoke URL provided in the blue ribbon at the top, since you’ll need this to test your deployment.
Test Your Deployment
You can test your deployment by making a GET call to the Invoke URL you copied in the previous step. You can use POSTMAN to invoke URL to get JWT token from Azure and then call the API URL by passing the token in it.
Get JWT Token
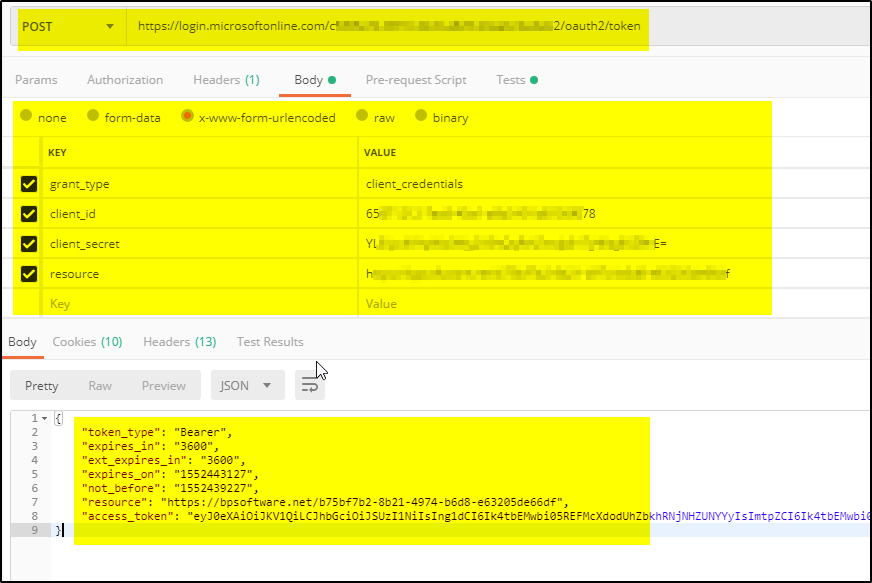
First, obtain a valid JWT Access Token. Use the below POST method and pass the parameters in BODY to get the JWT token (using POSTMAN)-
POST https://login.microsoftonline.com/<replace your tenantid here>/oauth2/token
BODY parameter:
grant_type:client_credentials
client_id:<Service principal Client id created in AAD>
client_secret:<replace athentication key value here>
resource:<APP ID URI of the Service Principal>
Invoke and access the API Gateway
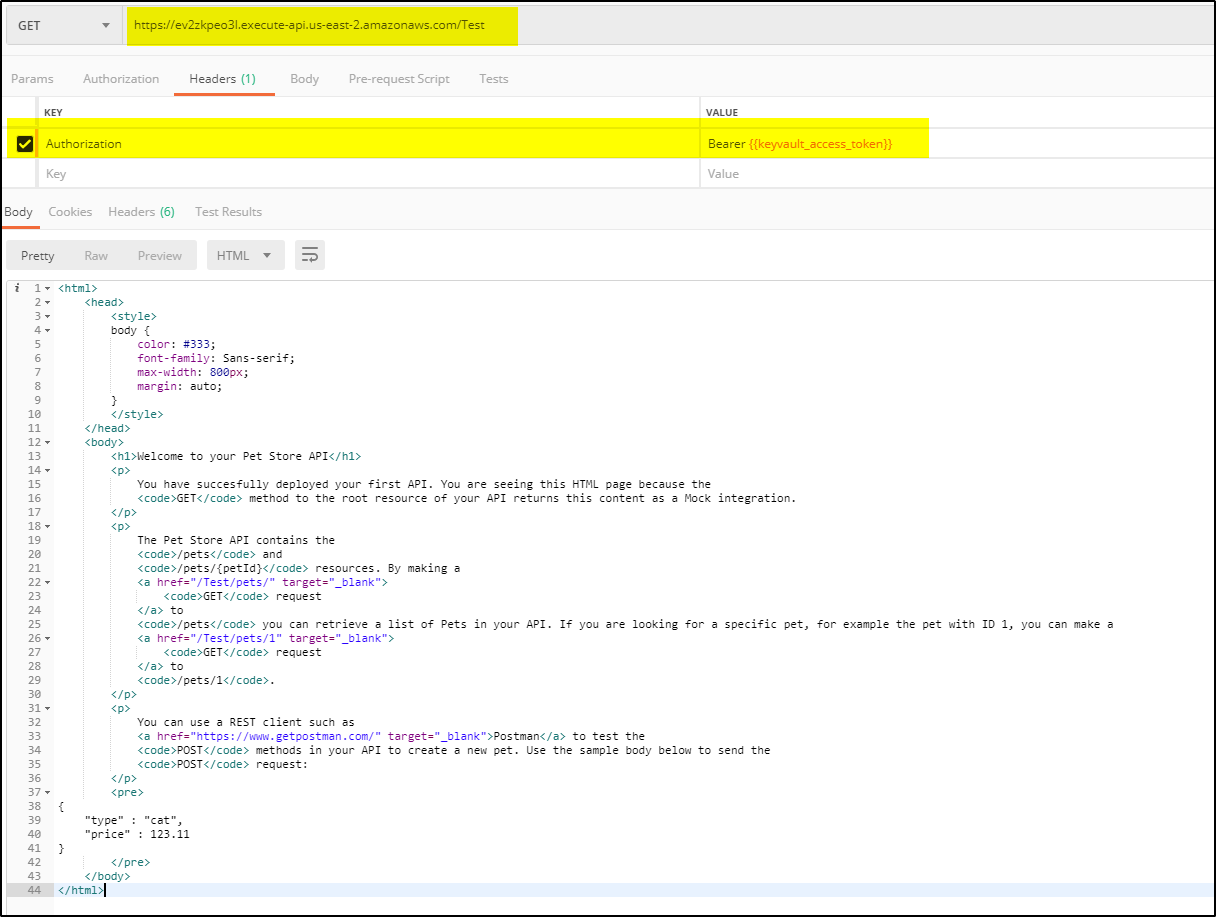
GET request https://ev2zkpeo3l.execute-api.us-east-2.amazonaws.com/Test
Headers parameter
Authorization: Bearer <replace the access_token value here>
This will return results as shown below-